Cyber Security Services

Assessment and Authorization
Assessment and Authorization (A&A) is a comprehensive examination of a company’s information system policies, security controls, protective rules, and documented cybersecurity vulnerabilities.
The A&A procedure assesses the efficacy and execution of a company’s security standards. This includes the organization’s policies and any external compliance requirements that the organization needs to meet. Then, an Authorizing Official examines the standard authorization package to verify the A&A examination (AO).
Access Controland endpoint detection
Threats posed by nation-states, hacktivists, organized crime, and malevolent and inadvertent insiders exist for businesses of all sizes. Endpoint security is one of the companies’ first locations to safeguard their networks.
The need for increasingly powerful endpoint protection solutions has increased with the number and complexity of cybersecurity threats. Endpoint protection systems are now designed to detect, analyze, prevent, and contain ongoing threats. They must work with other security technologies to speed up detecting, remediating, and responding to sophisticated threats.


Vulnerability assessment and management
Malicious actors may use a security hole to penetrate your network. Software and network security vulnerabilities are identified, prioritized, remedied, reported, and responded to via vulnerability management. Patching, software reconfiguration, and security policy upgrades may fix vulnerabilities.
Elementos prioritizes vulnerabilities based on risk-based remediation and data-driven analytics to prevent wasteful patching and downtime.
Intrusionand malware detection
An IPS complements an IDS by evaluating incoming traffic for harmful queries. A typical IPS setup secures applications using web application firewalls and traffic filtering. An IPS prevents attacks by discarding malicious packets and banning problematic IPs. Such a system employs a preexisting database for signature identification and can spot traffic and behavioral irregularities.
Some IPS systems have shortcomings despite blocking recognized attack vectors. Overdependence on established rules causes false positives. Elementos employs a mix of web application firewalls, customs rules, two-factor authentication, and back door protection to solve problems by intercepting connection requests to concealed backdoor shells. Since such queries can’t be faked, monitoring them helps find system backdoors.


Automated patch management system
Keeping systems and software updated reduces cybersecurity risk and optimizes endpoint system performance. Managing more workstations and servers increases risks and performance difficulties. Elementos’ Automate Patch Management software simplifies updating older systems and gives you granular control for peace of mind.
The correct Patch Management system can increase your organization’s security by addressing bugs and giving additional capabilities (identifying software that has ceased bug fixing so you can move to new software). Patches lessen the likelihood of systems failing due to faulty software and promote BYOD, which means a competent Patch Management Software can apply patches regardless of the device’s location.
Elementos prioritizes vulnerabilities based on risk-based remediation and data-driven analytics to prevent wasteful patching and downtime.
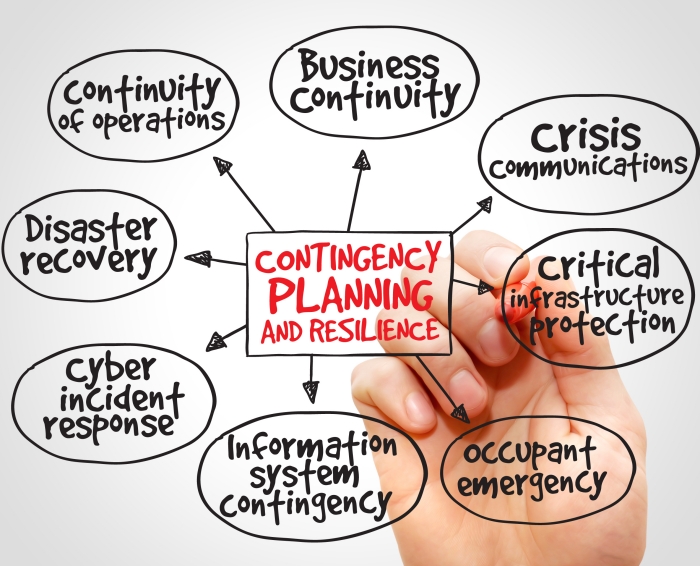
Business continuity planning
Business Continuity Planning (BCP) creates preventative and recovery mechanisms to cope with cyber risks or assure process continuity after a cyberattack. BCP also ensures operational continuity during catastrophe recovery.
Asset and personnel protection ensures a speedy recovery in a crisis. Business continuity involves maintaining vital operations during an emergency and recovering with as little downtime as feasible. A business continuity strategy addresses catastrophes, fires, disease outbreaks, cyberattacks, and other external hazards.
BCP enables a company to maintain critical operations during downtime. This allows the company to react swiftly to interruptions and create robust operating practices. A solid BCP saves money, time, and reputation/brand image. This reduces financial risks.

Employee Education
No matter how sophisticated your organization’s security technologies are, your personnel pose hazards. To estimate human risk, stakeholders must include deliberate, negligent, and compromised threats. Educating and empowering everyone who touches your network reduces risk by raising awareness and changing the culture.
Elementos provides end-user and role-based cybersecurity education. Meaningful, relevant, current training material builds a solid basis for your users, while simulated phishing attempts give insight and risk mitigation.
Get In Touch With Elementos
Call
(910) 691-2474

